CVE-2024-28232 – github.com/icewhaletech/casaos-userservice
Package
Manager: go
Name: github.com/icewhaletech/casaos-userservice
Vulnerable Version: =0.4.7 || >=0.4.7 <0.4.8
Severity
Level: Medium
CVSS v3.1: CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
CVSS v4.0: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:N/VA:N/SC:N/SI:N/SA:N
EPSS: 0.00262 pctl0.49336
Details
CasaOS Username Enumeration - Bypass of CVE-2024-24766 ### Summary The Casa OS Login page has disclosed the username enumeration vulnerability in the login page which was patched in `CasaOS v0.4.7`. ### Details It is observed that the attacker can enumerate the CasaOS username using the application response. If the username is incorrect the application gives the error "**User does not exist**" with success code "**10006**", If the password is incorrect the application gives the error "**User does not exist or password is invalid**" with success code "**10013**". ### PoC 1. If the Username is invalid application gives "User does not exist" with success code "**10006**". 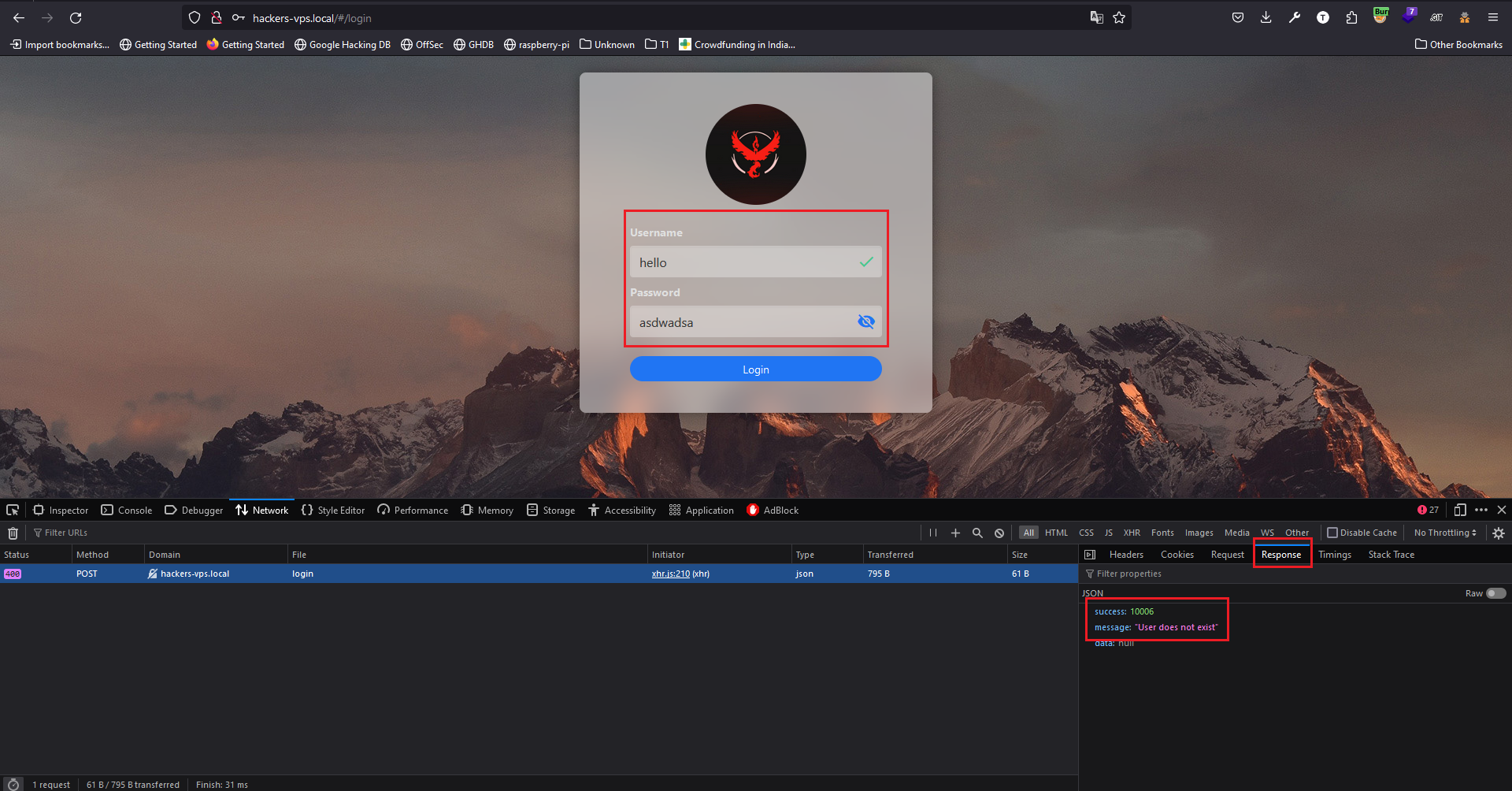 2. If the Password is invalid application gives "**User does not exist or password is invalid**" with success code "**10013**". 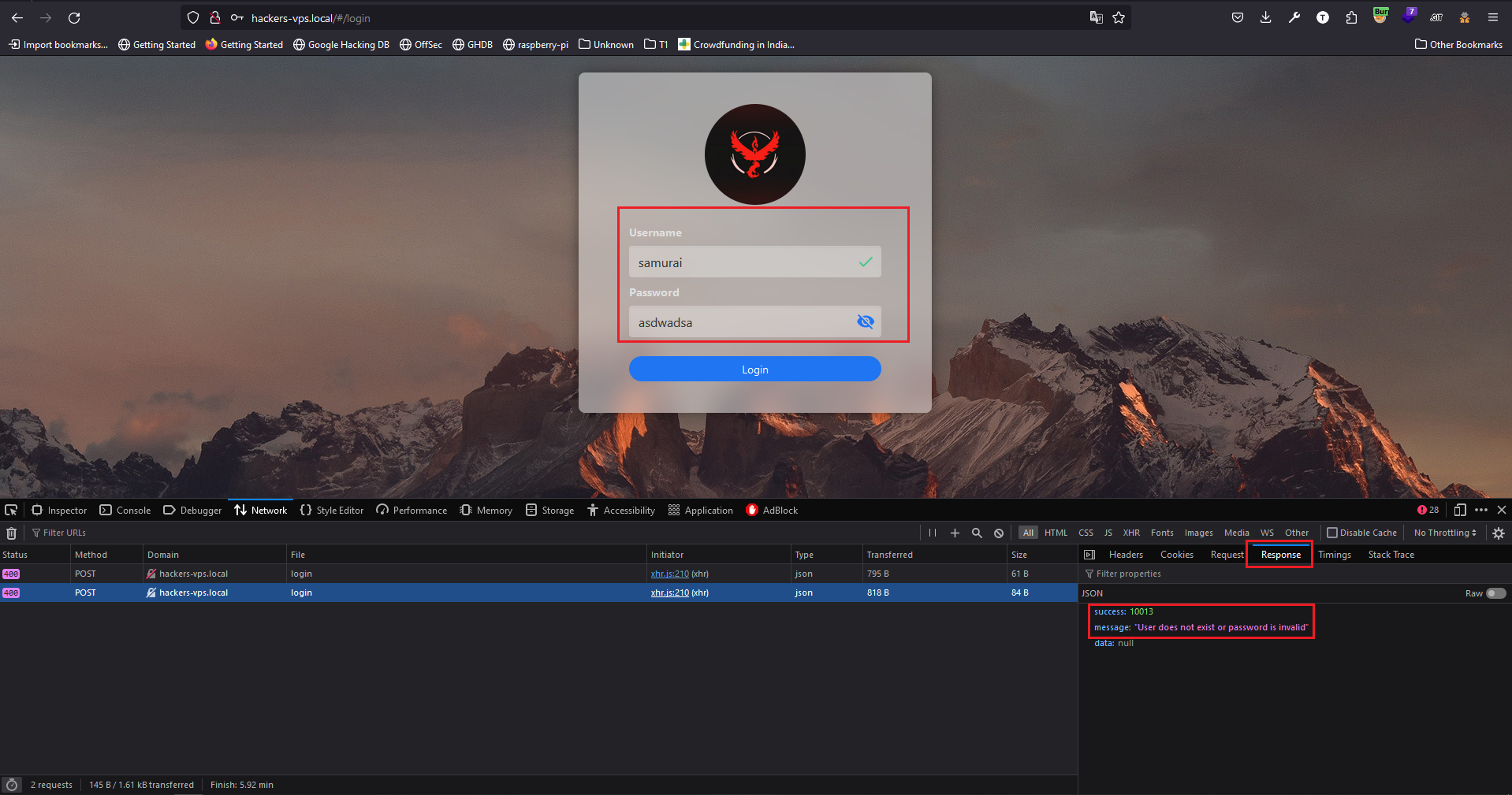 ### Impact Using this error attacker can enumerate the username of CasaOS. ### The logic behind the issue The logic behind the issue If the username is incorrect, then throw an error "**User does not exist**" with success code "**10006**", else throw an error "**User does not exist or password is invalid**" with success code "**10013**". This condition can be vice versa like: If the password is incorrect, then throw an error "**User does not exist or password is invalid**" with success code "**10013**", else throw an error "**User does not exist**" with success code "**10006**". ### Mitigation Since this is the condition we have to implement a single error which can be "**Username/Password is Incorrect!!!**" with single success code.
Metadata
Created: 2024-04-01T15:48:15Z
Modified: 2024-04-03T18:59:29Z
Source: https://github.com/github/advisory-database/blob/main/advisories/github-reviewed/2024/04/GHSA-hcw2-2r9c-gc6p/GHSA-hcw2-2r9c-gc6p.json
CWE IDs: ["CWE-204"]
Alternative ID: GHSA-hcw2-2r9c-gc6p
Finding: F026
Auto approve: 1
