GHSA-4g2x-vq5p-5vj6 – @budibase/server
Package
Manager: npm
Name: @budibase/server
Vulnerable Version: >=0 <2.20.0
Severity
Level: Critical
CVSS v3.1: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSS v4.0: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N
EPSS: N/A pctlN/A
Details
Budibase affected by VM2 Constructor Escape Vulnerability ### Impact Previously, budibase used a library called `vm2` for code execution inside the Budibase builder and apps, such as the UI below for configuring bindings in the design section. 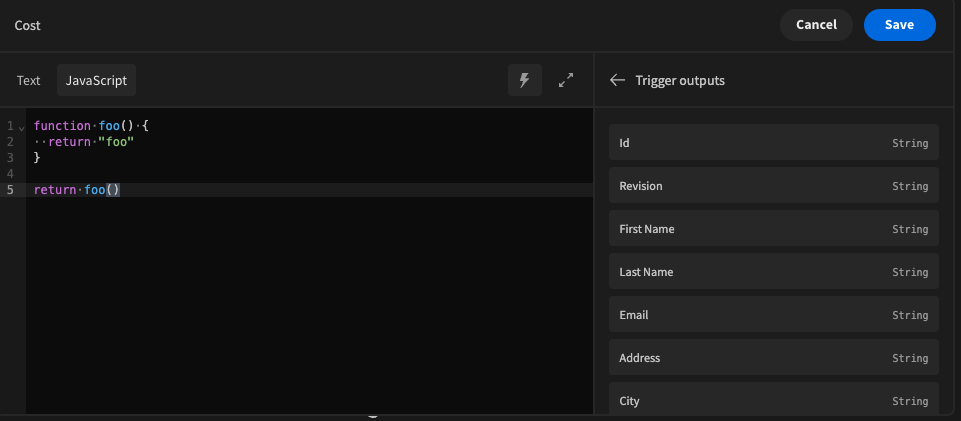 Due to a [vulnerability in vm2](https://github.com/advisories/GHSA-cchq-frgv-rjh5), any environment that executed the code server side (automations and column formulas) was susceptible to this vulnerability, allowing users to escape the sandbox provided by `vm2`, and to expose server side variables such as `process.env`. It's recommended by the authors of `vm2` themselves that you should move to another solution for remote JS execution due to this vulnerability. ### Patches We moved our entire JS sandbox infrastructure over to `isolated-vm`, a much more secure and recommended library for remote code execution in 2.20.0. This also comes with a performance benefit in the way we cache and execute your JS server side. The budibase cloud platform has been patched already and is not running `vm2`, but self host users will need to manage the updates by themselves. If you are a self hosted user, you can take the following steps to reproduce the exploit and to verify if your installation is currently affected. Create a new formula column on one of your tables in the data section with the following configuration. 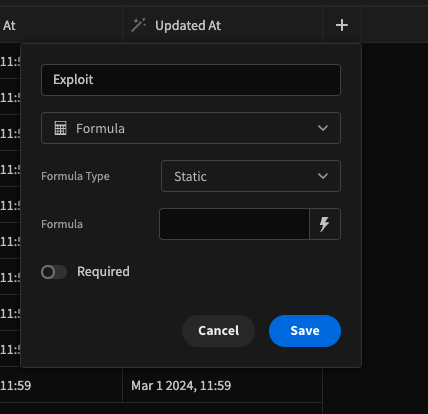 Add the following JS function to the formula and save. 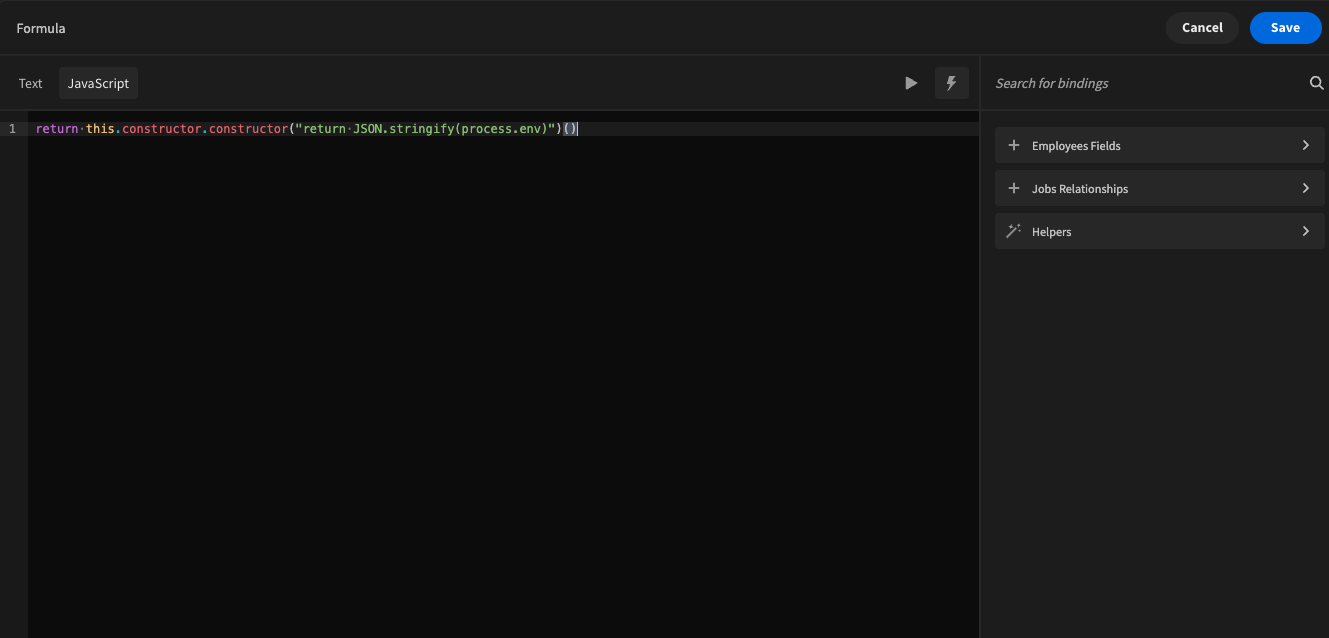 If your installation is vulnerable, when the formula evaluates you will be able to see the printed `process.env` in your new formula field. If not, your installation is not affected. ### Workarounds There is no workaround at this time for any budibase app that uses JS. You must fully migrate post version 2.20.0 to patch the vulnerability. ### References - https://github.com/advisories/GHSA-cchq-frgv-rjh5
Metadata
Created: 2024-03-01T20:09:00Z
Modified: 2024-08-15T17:02:27Z
Source: https://github.com/github/advisory-database/blob/main/advisories/github-reviewed/2024/03/GHSA-4g2x-vq5p-5vj6/GHSA-4g2x-vq5p-5vj6.json
CWE IDs: ["CWE-94"]
Alternative ID: N/A
Finding: F422
Auto approve: 1
