CVE-2024-24808 – pyload-ng
Package
Manager: pip
Name: pyload-ng
Vulnerable Version: >=0 <0.5.0b3.dev79
Severity
Level: Medium
CVSS v3.1: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
CVSS v4.0: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:P/VC:L/VI:L/VA:N/SC:N/SI:N/SA:N
EPSS: 0.01394 pctl0.79652
Details
pyLoad open redirect vulnerability due to improper validation of the is_safe_url function ### Summary Open redirect vulnerability due to incorrect validation of input values when redirecting users after login. ### Details pyload is validating URLs via the `get_redirect_url` function when redirecting users at login. 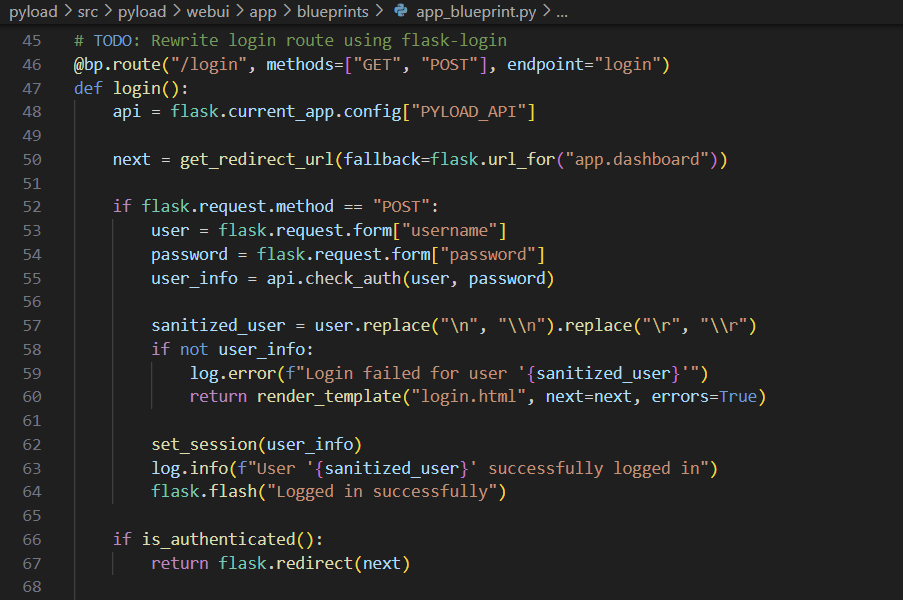 The URL entered in the `next` variable goes through the `is_safe_url` function, where a lack of validation can redirect the user to an arbitrary domain. 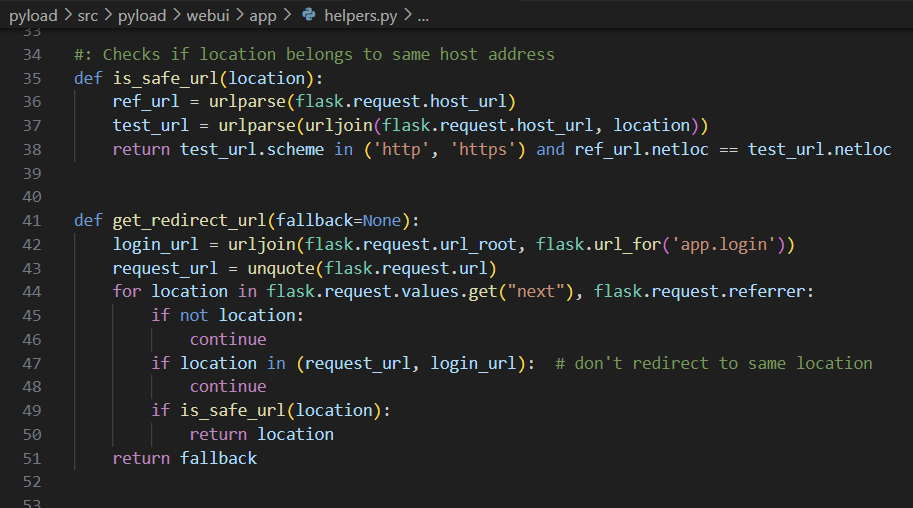 The documentation in the urllib library shows that improper URLs are recognized as relative paths when using the `urlparse` function. (https://docs.python.org/3/library/urllib.parse.html#urllib.parse.urlparse) For example, When an unusual URL like `https:///example.com` is entered, `urlparse` interprets it as a relative path, but in the actual request it is converted to `https://example.com` due to url normalization. ### PoC 1. In the next variable, insert the URL to which you want to redirect the user. 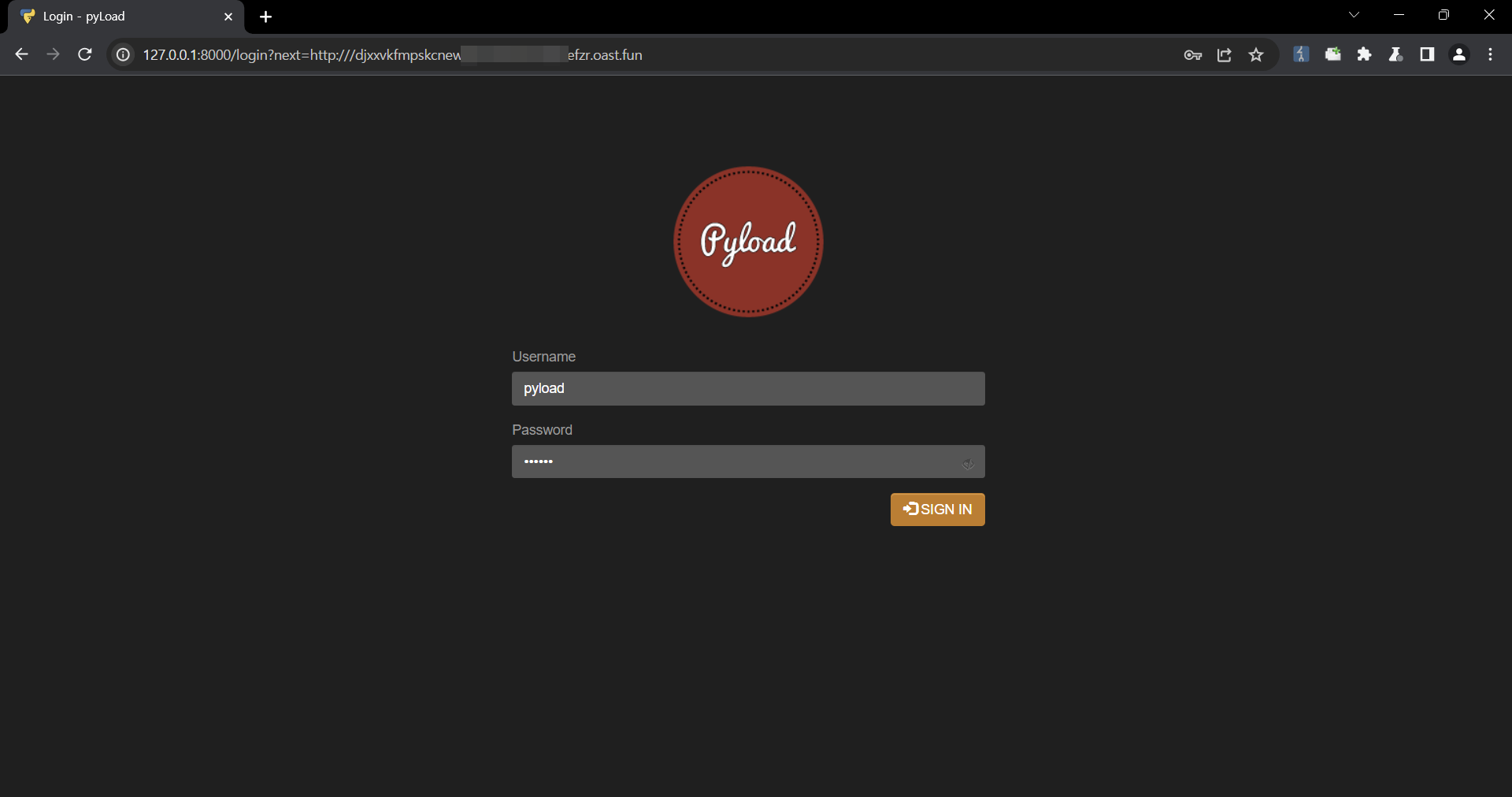 2. Check that it is possible to bypass url validation and redirect users to an arbitrary url. 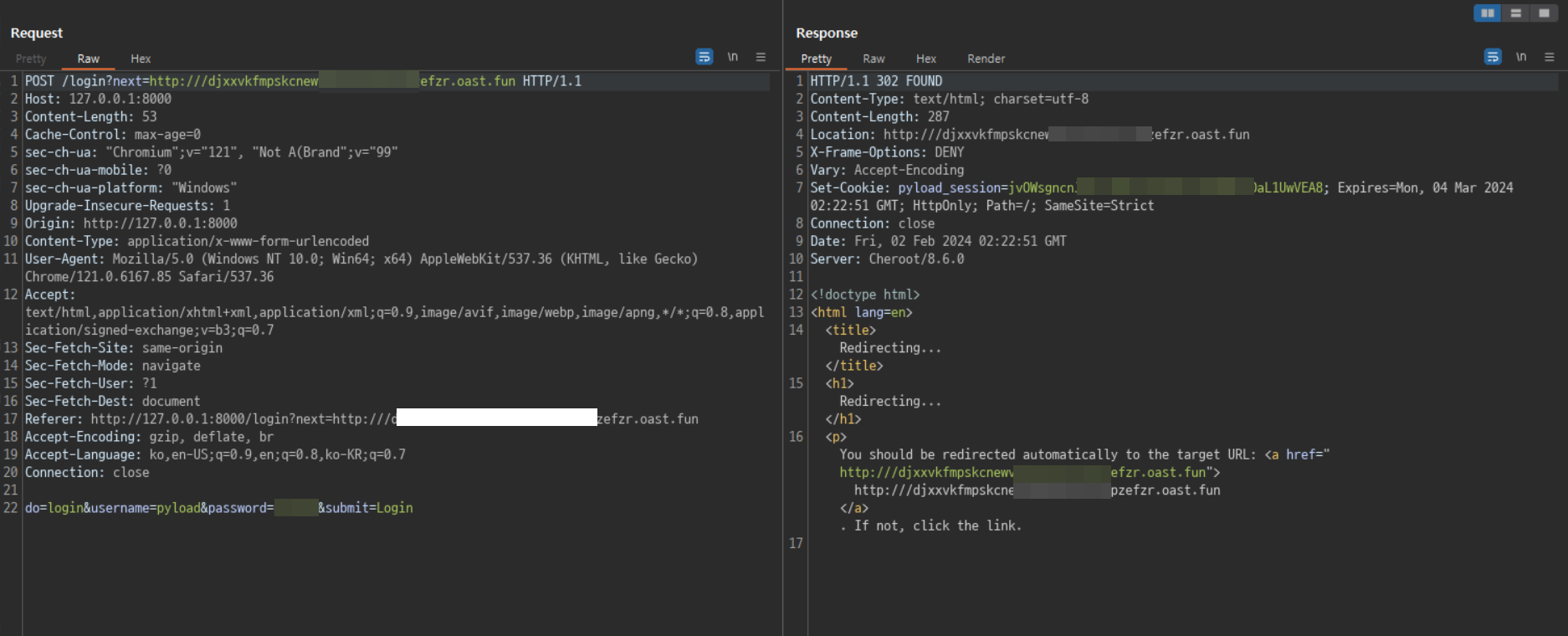 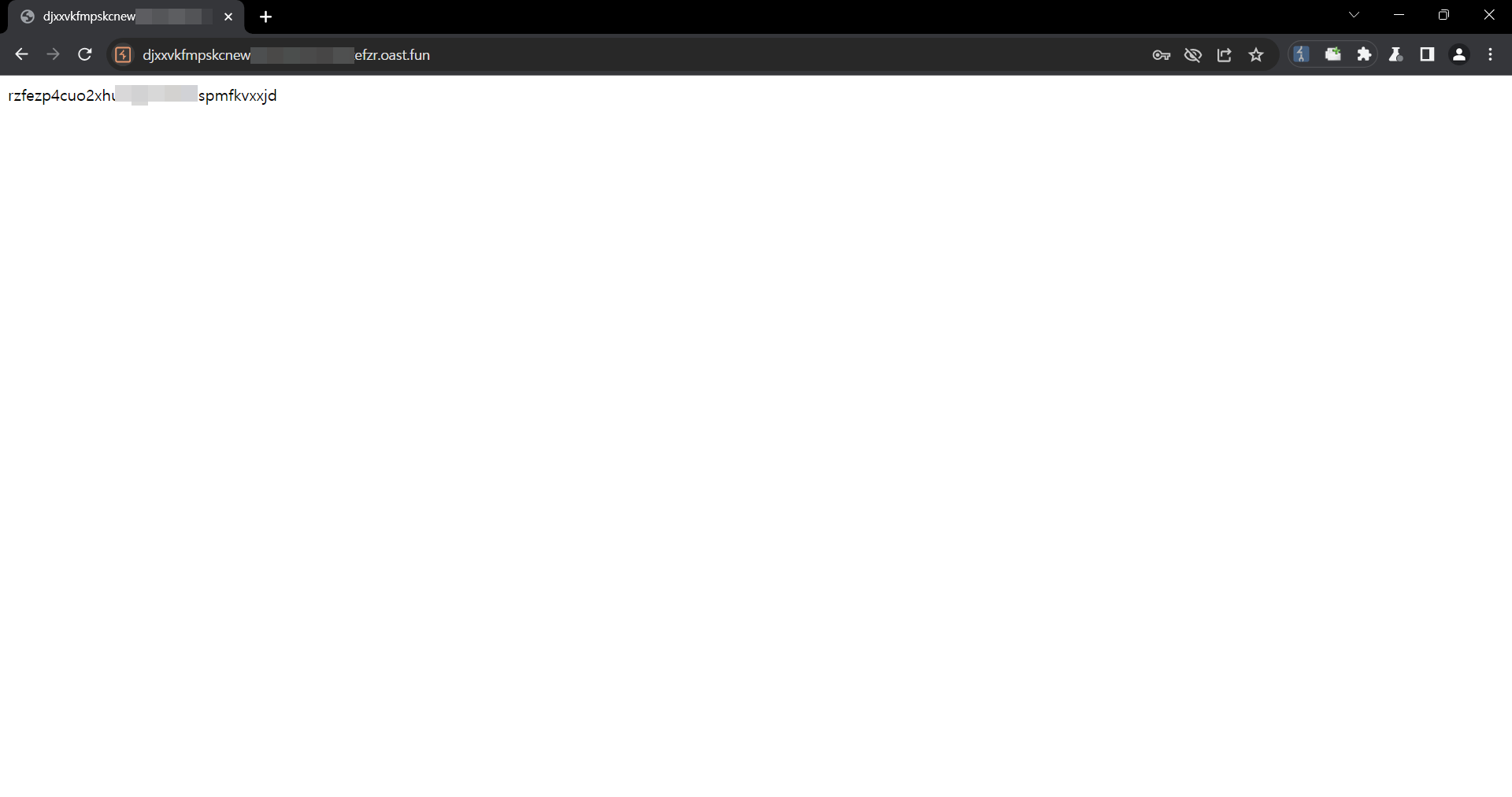 ### Impact An attacker can use this vulnerability to redirect users to malicious websites, which can be used for phishing and similar attacks.
Metadata
Created: 2024-02-05T23:23:22Z
Modified: 2024-02-14T14:51:14Z
Source: https://github.com/github/advisory-database/blob/main/advisories/github-reviewed/2024/02/GHSA-g3cm-qg2v-2hj5/GHSA-g3cm-qg2v-2hj5.json
CWE IDs: ["CWE-601"]
Alternative ID: GHSA-g3cm-qg2v-2hj5
Finding: F156
Auto approve: 1
